-

Is ID.me safe? A complete guide to digital identity protection
ID.me, a digital identity-verification service used by government agencies and many private organizations, has come under scrutiny in recent years. Privacy-related and ethical concerns about facial-re...
-
Discord malware: How to stay safe and clean your device
As one of the most active communication platforms, Discord attracts a wide range of communities, and, unfortunately, attackers who want to exploit that activity. Discord’s built-in file sharing, lar...
-

Is your Facebook account cloned? How to detect it and protect yourself
If you’ve suddenly started receiving messages from friends asking whether you created a “new” profile, your Facebook account might have been cloned. Account cloning, when someone copies your pho...
-

What is HIPAA compliance? What you need to know
Every time you visit a doctor, fill a prescription, or use a telehealth app, sensitive information about your health is collected and stored. If that data isn’t handled properly, it can lead to loss...
-

What is IIoT and why its security matters more than ever
In modern industry and operations, more devices than ever are connected to networks and each other through the Industrial Internet of Things (IIoT). This connectivity allows factories, plants, utiliti...
-

How can you protect your home computer?
Many people underestimate how vulnerable their personal computers are. Without corporate-grade defenses or IT oversight, home setups are often easy targets. At the same time, new trends such as malwar...
-
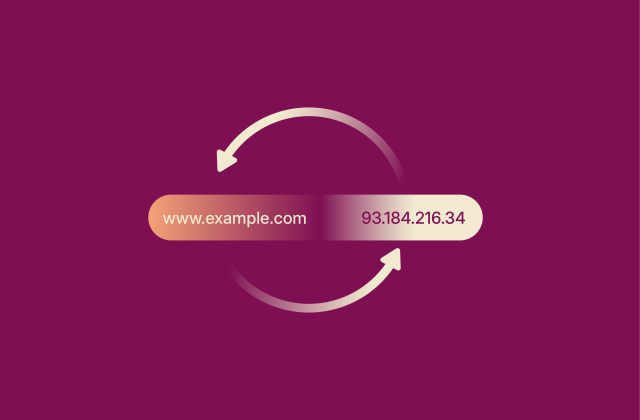
The ultimate guide to recursive DNS: Everything you need to know
The internet runs on a complex system called the Domain Name System (DNS) that turns human-readable domain names into machine-readable IP addresses. A recursive DNS server is a vital part of this syst...
-

What is computer networking and how VPNs fit in
Computer networks form the backbone of modern digital communication. Learning how these networks operate will help you better understand the modern digital landscape and make smarter decisions about p...
-

Domain hijacking vs. DNS poisoning: Key differences and how to stay protected
Domain-based attacks, which target the control or resolution of internet domains, are one of the major cyber threats of today. Two common and high-impact forms of domain-based attacks are domain hijac...
-

A complete guide to MPLS VPN services for secure and reliable connectivity
In enterprise networking, the choice of how to connect offices, data centers, and remote users has a direct impact on performance, reliability, and cost. One solution is a multiprotocol label switchin...

This content is not available in your region
To continue, please visit our dedicated website for the United Arab Emirates.
ExpressVPN for UAE 